You can think of AWS CloudShell to having ssh access to an Amazon Linux EC2 instance in your region at all times (without actually creating an EC2 instance on your own, which incurs cost).
Let’s explore
You can become root by doing
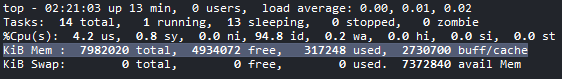
sudo bashLooking at top
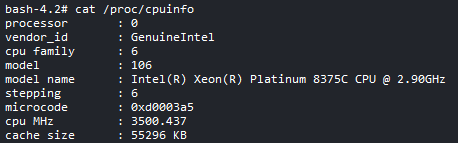
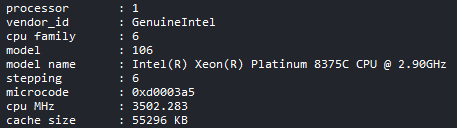
Result of cat /proc/cpuinfo
Quite beefy vCPUs also.
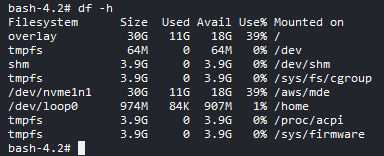
Storage
Can install packages using yum install.
Can immediately run AWS CLI (as cloudshell-user, not root)
For example
aws s3 lsWhat’s good about it
Because it comes preconfigured with your AWS credentials and AWS CLI, you can start using AWS CLI straight away, e.g. listing you S3 buckets, testing downloads and uploads from/to S3 buckets, SSH to your EC2 instances in the region (via their public IP addresses), etc
Can you host a server (e.g. web server) on it?
That’s a bit cheeky to do, and the answer is no. To be a server, you will need to know the IP address of the CloudShell instance, you can figure that out by doing a wget in CloudShell to a server that you control e.g. wget http://zestycoder.com, then check at your controlled server, what IP was used by wget (which would be CloudShell). I notice that the IP changes from time to time. And you cannot connect to the CloudShell’s IP address (times out, so probably firewalled or NATed).
Actually I just lied, you kinda can. But since it is going to be unreliable (you’ll never know when the CloudShell machine will get terminated). Here’s how
In CloudShell
yum install nginx
echo 'Welcome to CloudShell' > /var/www/html/index.html
apachectl -k start
wget localhost <- to test, you should get a page with the text "Welcome to CloudShell"
cat > key.pem <- copy paste an SSH private key that can connect to an EC2 instance, let's call this instance andromeda
chmod 400 key.pem
ssh -i key.pem root@andromeda-ip-address -R9080:localhost:80 <- connect to andromeda and setup a remote port forwarding SSH tunnelIn andromeda do these steps
apt install nginx
rm /etc/nginx/sites-enabled/default
cat > /etc/nginx/sites-available/proxy
server {
listen 80;
location / {
proxy_pass http://127.0.0.1:9080;
}
}
ln -s /etc/nginx/sites-available/proxy /etc/nginx/sites-enabled/proxy
systemctl restart nginxWhen you do a netstat you should see the SSH tunnel from CloudShell and nginx running as a reverse proxy at port 80. Notice that the SSH tunnel is listening on localhost, thus necessitates the need of running a reverse proxy.
# netstat -nutap
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:9080 0.0.0.0:* LISTEN 31738/sshd: root@pt <- SSH tunnel from CloudShell
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 653/sshd: /usr/sbin
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN 334/systemd-resolve
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 31836/nginx: master <- nginx listening on port 80 acting as reverse proxyFrom my home computer, visiting andromeda’s IP address, I get CloudShell’s nginx
The flow is thus, from my browser to andromeda’s nginx, running as a reverse proxy, it gets forwarded andromeda’s localhost on port 9080, it goes “through” the tunnel, eventually arriving at CloudShell’s nginx running on port 80.